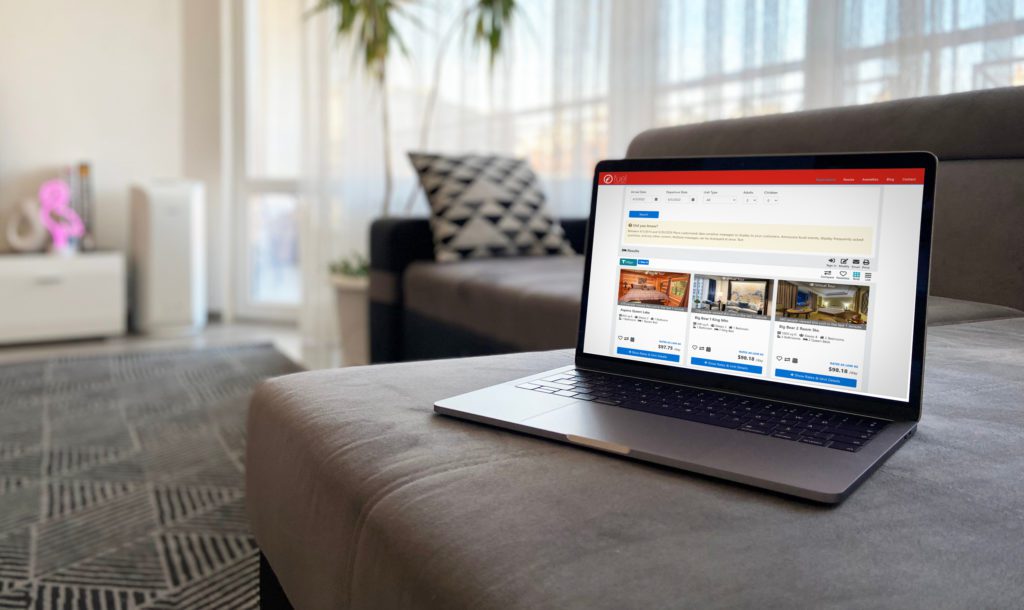
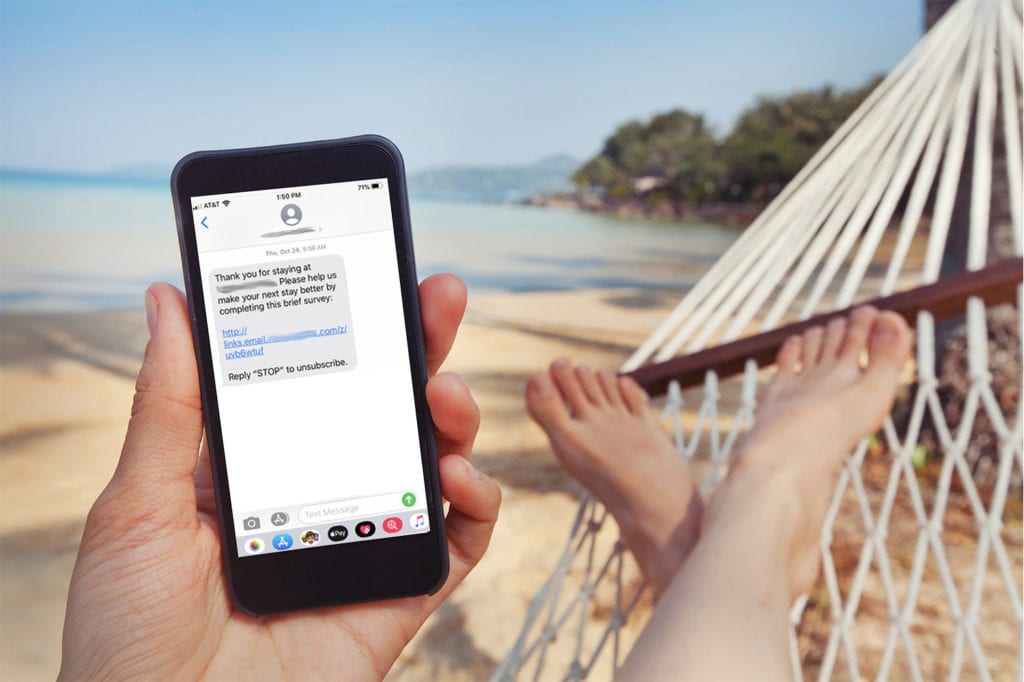
When evaluating a potential booking engine vendor, hotels have many things to balance. First and foremost, core features like real-time integration with key systems. Your booking engine should be designed to convert based on consumer behavior and expectations. Secure payment processing is also a non-negotiable for any booking engine. For more, read: What to Look for […]
News
Maximizing Hotel Revenue: How Software Solutions Drive RevPAR Growth
Optimizing Revenue per Available Room (RevPAR) is one of the key focuses of most hoteliers. Travel is up, but so are guest expectations. Navigating the complex world of revenue management requires innovative solutions. While dedicated revenue management software is a component of this process, all of your technology must work together to increase your bottom […]
What to Look for in Hotel Booking Software: Elevating Guest Experience and Hotel Success
If your hotel is considering ways to increase direct bookings, what to look for in hotel booking software is an important consideration. The right booking engine is a crucial decision that significantly impacts both guest experience and your overall success. As you navigate the many options available, it’s essential to understand what key features contribute […]
How to Respond to a Negative Hotel Guest Review
Online reviews have an enormous impact on potential guests’ booking decisions. Negative hotel guest reviews significantly impact a property’s reputation and the likelihood a guest will book, or a happy guest will return. According to one study by Brightlocal, 94% of consumers said they avoid businesses with negative reviews. And keeping your overall score high […]
10 Hotel Direct Booking Strategies that Work
There’s no instant way to improve your direct bookings, but these hotel direct. booking strategies combined with our hotel software systems can enhance the guest experience from pre-booking and beyond. Employing our industry-leading technology can provide customer-first, focused tactics to give your hotel the edge over OTAs and third-party sites. Read on to learn four […]
Hotel Email Marketing Examples: 10 Automated Emails Your Hotel Should Be Sending
Hoteliers, the spray and pray approach to email is dead. Start utilizing consumer data to your advantage with triggered, rule-based and segmented email sends. Click below to learn more about the automated emails your hotel should be sending.
How to Improve Hotel Check-In Process – 7 Simple Solutions
The hotel check-in process has long been an important, albeit tedious step in a hotel guest’s to-do list. But it’s becoming much easier to improve the hotel check-in process thanks to an advancement in user-friendly hotel software systems. Which is good, because improving guest satisfaction is becoming increasingly important for hotels to accomplish. In fact, […]
Booking Engine for Independent Hotels: 5 Things to AVOID
You may have an idea of what you want in a booking engine for your independent hotel. But do you know what should be 100% avoided when looking for a new booking engine? The quality of the technology you implement on your hotel website should not be ignored. Otherwise, you risk encountering many the pitfalls […]
4 Ways to Earn More Direct Hotel Bookings
Direct hotel bookings are reservations that a guest makes directly with a property. A direct booking is made with the hotel itself, rather than via a third-party such as an online travel agent, meta-search site, a managed travel service, or similar. The term ‘direct bookings’ typically refers to stays that are still booked online, usually […]
8 Reasons Why Mobile Keys are Taking Over in Hotels
The hospitality industry has witnessed a significant shift towards digitalization, leading hotels to adopt digital keys as a way of improving internal operations, reducing costs, increasing direct sales, and enhancing hotel guest satisfaction. But if you’re still not convinced about the benefits of a hotel digital key and lock solution, you’ve come to the right […]
6 Hotel Guest Communication Tips to Master
Technology helps you keep in touch with guests before, during, and after their stay. When most hotels think of hotel guest communication tips, your first thought is front desk staff training. But there’s more to it than that. Guest communication starts long before the front desk. Your internet presence and specialized software are key to […]